Avoiding Tor Panic

 Operation Onymous brought down Silk Road 2 and a number of other high profile dark net sites. The statements from law enforcement are extremely over broad and meant to intimidate the would-be founder of Silk Road 3 from even trying.
Operation Onymous brought down Silk Road 2 and a number of other high profile dark net sites. The statements from law enforcement are extremely over broad and meant to intimidate the would-be founder of Silk Road 3 from even trying.
Then we learned that a third of the four hundred sites were all in a single hosting facility, presumably one that was slack on checking identities of those renting servers. Then we learned that another third of the sites were simply older host keys for the same operations, leftovers from the last time the Tor Project told everyone to upgrade their software and rekey their systems. Law enforcement has scored an impressive victory, but it isn’t the dark net apocalypse they would have us believe.
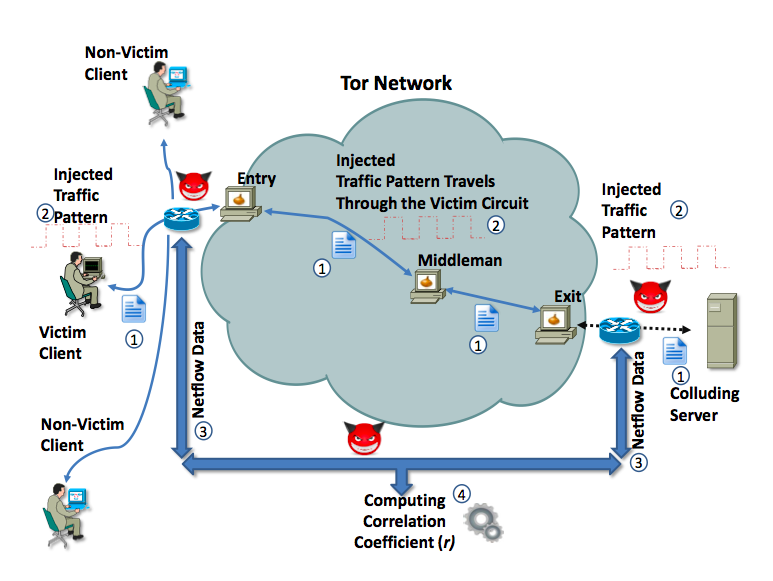
The situation isn’t helped by unskilled authors who plunge into deep, shark infested waters like those of a fourteen page academic paper with the ponderous title On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records and come back with a breathless tale of Tor users being identified by “exploiting routers”. The paper does have a nice diagram of what they were doing and which will help to demystify things a bit.
Tor Alone is not the Privacy Panacea
The paper’s detection method is based on the use of Cisco’s net flow accounting protocol, it’s offspring such as Juniper’s j-flow, and the open standard s-flow, all of which report network utilization to applications used for capacity planning and troubleshooting. The paper presumes that the Tor user is facing a “powerful adversary”. This adversary already controls a server the target user visits and that the service provider who owns the router is willingly sharing their network traffic accounting data. The method of identifying the user was changing rate limits on downloads when the user was accessing a very large file. The red devils on the diagram represent all the places the “powerful adversary” has absolute mastery of the network; I wanted to replace them with unicorns.
Most of the administrators of the servers that were taken down are in custody or in hiding, but among the vanished was doxbin, an identity theft oriented sites operated by a hacker named nachash. I have known him for a couple of years and when I noticed his site was down I visited him on IRC to see if he’d share any of the details. We discussed his theories on what had happened and a bit later he made a cheeky post to the Tor developers list, yes hello, internet super villain here . What seems to have occurred is an 0day exploit targeting the Tor software itself, not an outright intrusion but something that could put a significant load on the server, and this may have been used to force server operators to log in to their systems.
There isn’t a cause and effect link between that paper and Operation Onymous, nor does it warrant an ominous headline coupled with a summary authored by someone who doesn’t understand the technology. If you are a worried Tor user here are two things I suggest which will let you sleep better.
- The Tor Project browser bundle displayed a vulnerability that was exploited during the Freedom Hosting investigation in 2013. A potential cure for that is a gateway/workstation virtual machine setup called Whonix , which won’t give up your location or details about your real computer even if it does have a vulnerability.
- The bigger the Tor network is the faster it runs and the harder it is to compromise. If you run an exit node you’ll deal with DMCA complaints, but you just contribute a relay node it just silently adds capacity. You can get a minimal Linux VPS from Virpus for $5 monthly and add over a terabyte of throughput to the network.
Tor alone is not the privacy panacea its promoters would have you believe. If you’re going in harm’s way you should have Whonix or a similar dual virtual machine configuration. Using Tor does not absolve you from other network security measures such as a VPN that ensures your first step on the Tor network starts in a privacy friendly jurisdiction on another continent.
What do you think about Tor privacy and security after the recent events? Comment below!
Images from Tor and Shutterstock.